With the transition of most of important company data to electronic form, gaining access by an unauthorized person to a computer network can pose a potential security threat to companies.
Network security
Firewall solutions
CompuNet offers Fortinet products and services that provide broad, integrated, and robust protection against dynamic security threats while simplifying the IT security infrastructure.

Fortinet’s core product line is the FortiGate family of devices, which protect applications and networks against threats and are accelerated by ASIC processors. These devices integrate a number of security and network functions, see the picture.
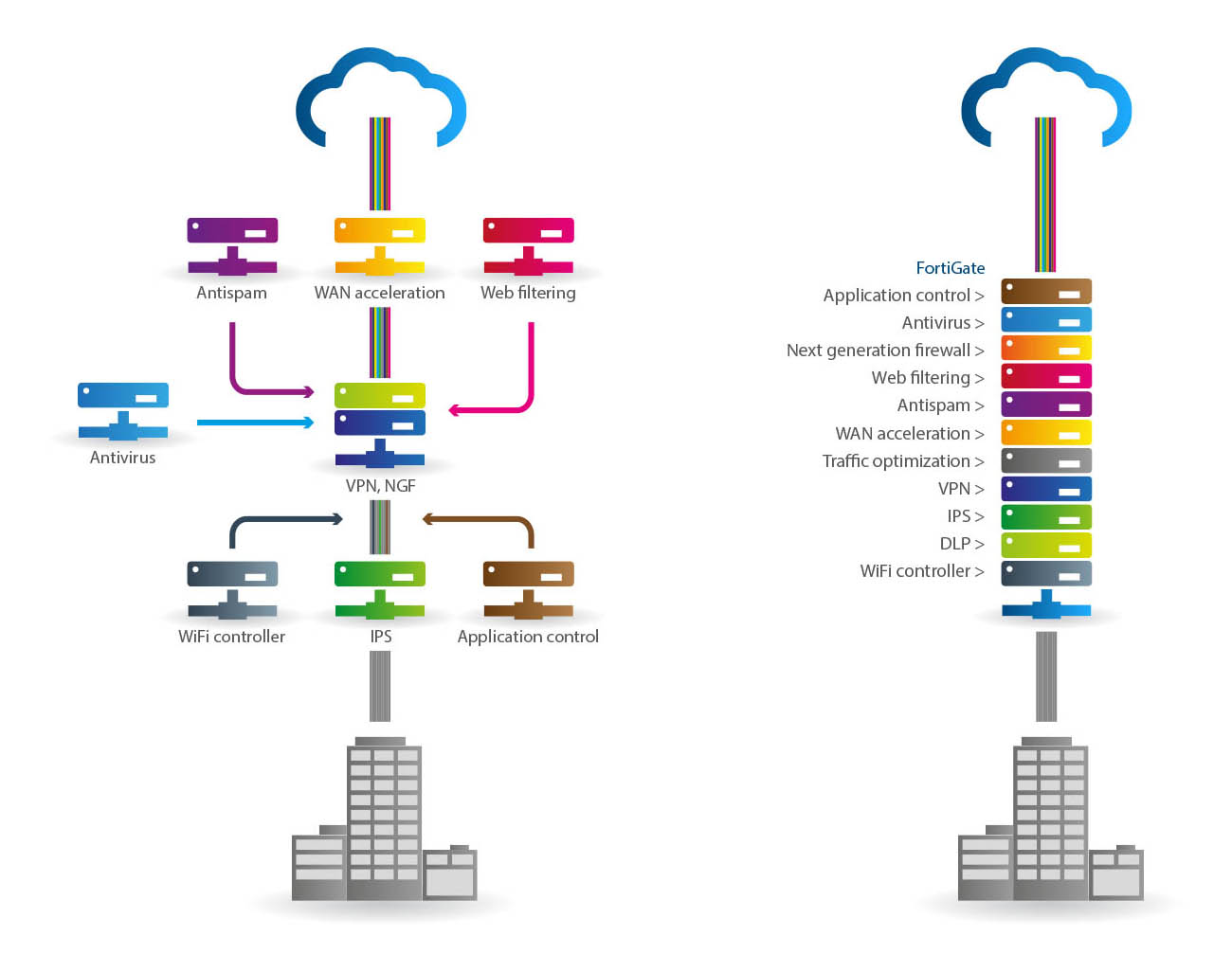
Overview of the full Fortinet offering
The scope of the Fortinet products range goes beyond UTM. Its goal is to secure an organization’s IT infrastructure starting from the endpoints through the perimeter to the core of the network, including databases and applications. All devices offer the broadest range of security and network features on the market, see the picture.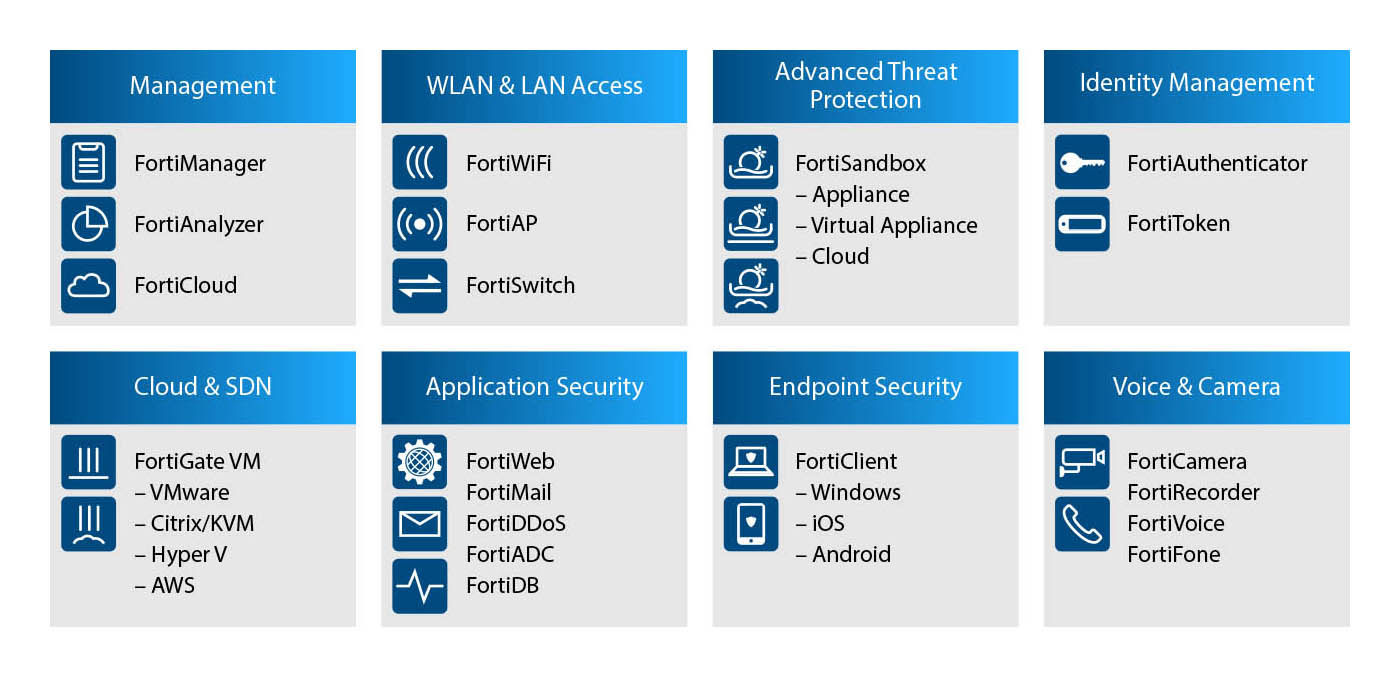
IPS – Intrusion Prevention Systems
Solutions for mitigating the risk of impact of security threats
As network communication becomes ever more pervasive, also attempts to exploit vulnerabilities of devices, operating systems or applications over the network increase on intensity. In response to these threats, which firewalls and proxy servers unfortunately cannot effectively prevent, a new category of devices generally referred to as network Intrusion Prevention Systems (network IPS) appeared.
CompuNet offers TippingPoint IPS solutions, which are hardware appliances that inspect data traffic in-line without any detectable loss of performance or modifications to the legitimate traffic. However, at high speeds and with minimal latency, they are able to monitor data traffic on the application level and they block any unwanted traffic in real time. These devices integrate Next-Gen firewall and IPS device features.
SandBox
Fortinet
CompuNet offers Fortinet products and services that provide broad, integrated, and robust protection against dynamic security threats while simplifying the IT security infrastructure.

TrendMicro
Deep Discovery Analyzer performs security simulations of endpoint PC workstations including the installed software. It performs a detailed analysis of the behaviour of a wide range of Windows executables, Microsoft Office documents, PDF documents, web content, emails and compressed files. It detects malware hidden in these resources and issues alerts on targeted attacks and security threats specific to a given user environment. It generates a detailed record of the performed analysis and forwards the information further to trigger necessary defence measures at the level of individual network elements.
802.1X
Protection of the network against unauthorised access
With the transition of most of important company data to electronic form, gaining access by an unauthorized person to a computer network can pose a potential security threat to companies. For this reason, it is necessary to protect against unauthorised access. Protection against unauthorised access does not mean protecting physical access to active networking elements or computer cabling, but mainly adopting measures to prevent connecting a laptop, a wireless access point or a network analyser to the network at any point. By controlling network access, it is possible to precisely specify in the individual networking devices a group of devices or users who can connect via the respective device. Other devices/users will then not be allowed into the network by temporarily or permanently blocking the physical port through which they attempted to connect to the network without authorization.NetworkLogin 802.1x
Securing a computer network with NetworkLogin 802.1x allows active networking devices to securely authenticate a user with a user name and password and provide access to network resources only upon successful authentication. In this case, the active networking device can be a switch, an access server, a wireless access point (AP). The authentication authority is not the active networking device itself, but a central user database with which the networking device communicates as a client. The database is referred to as RADIUS (Remote Authentication Dial In User Service – RFC 2865). A RADIUS server can be operated as a service integrated in Microsoft Active Directory. During the authentication process, the station (referred to as the Supplicant in the 802.1x terminology) connects to a port secured by 802.1x. It notifies the switch of its existence by sending any packet, for example an IP address assignment request. Subsequently, the switch does not forward the received DHCP request further and it sends a request for identification back to the station instead. The station responds by sending its user name and password. The switch encrypts the received information and sends it to the authentication authority. The RADIUS server processes the received information and sends user confirmation or rejection back to the switch. Based on this information, the switch grants or denies the station access to the secured network.GAMA and BYOD
BYOD, standing for “Bring Your Own Device”, is a popular trend where employees are allowed to bring their own smart devices (such as laptops, smart phones, tablets) to the corporate environment. This, of course, increases the pressure on IT security. BYOD makes IT security more challenging as it introduces conflicting requirements for security, employee productivity and convenient use.
GAMA BYOD
Our own solution is GAMA BYOD. To add a new BYOD device, the user just enters the device name and unique access credentials are generated automatically. After that, the device can be connected to an SSID with forced 802.1x authentication and, when logging in for the first time, the device will automatically ask for access credentials. Access credentials are automatically reserved for a specific device after the first login.- A user with access rights can grant network access to his/her own devices or to guests via a web browser.
- The users generate a unique name and password for their devices.
- When the device is connected to the SSID, it will automatically ask for the generated name and password.
- 802.1x authentication is enforced by the SSID, being a standard that all devices easily support.
- The encryption key for communication between the AP and client devices is generated dynamically by the 802.1x protocol.
- Users can assign access to their devices, but also to the devices of their guests. These, of course, are connected to a separate VLAN.
- The solution supports Android, BlackBerry, iPhone and Windows mobile platforms.
Key features
- Controlling employee access to WLAN
- Account management
- Statistics
- Integrated Radius Server
- LDAP user authentication, e.g. Active Directory
- MAC address authentication
- Collaboration with devices supporting RADIUS and 802.1x
- Portal authentication
- High availability (cluster support)
Key benefits
- Support for BYOD policy for employees.
- Managed network access for employee devices.
- SYSLOG containing related security events.
- High availability (cluster support)
GAMA – Guest Access Manager
GAMA is a robust and secure system for managing guest access to a wireless network with simple user interface. The system runs on Linux, which runs as a virtual machine in VMWare.GAMA Guest Access Manager
A user with access rights can grant guest access to the network. The system controls can be accessed via any web browser and they can be integrated into the customer’s website. The guest is connected to a WiFi network and is dynamically assigned an IP address. After launching a web browser and attempting to access any web page, the browser is automatically redirected to the wireless switch’s internal web page for authentication.CLEAR PASS
A solution for networks that need a gatekeeper function capturing information about anyone who connects to the network including from which device. It securely manages network access and enforces security policies on other interconnected networking elements based on context sharing, automatic discovery and profiling of users, their devices, including IoT fingerprinting.SLA
CompuNet provides the following services to its customers:
- HW service (HP, Fortinet).
- Guaranteed repair times.
- Device recovery.
- Customized SLAs.
- We provide telephone support.
- Penetration testing.
